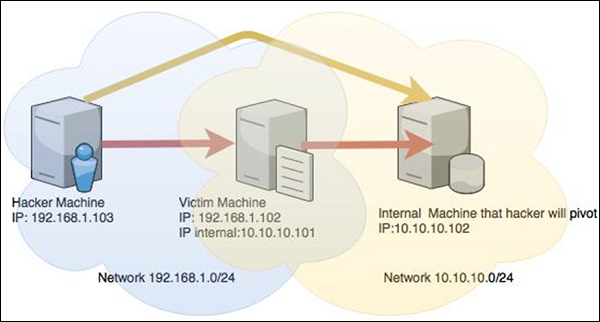
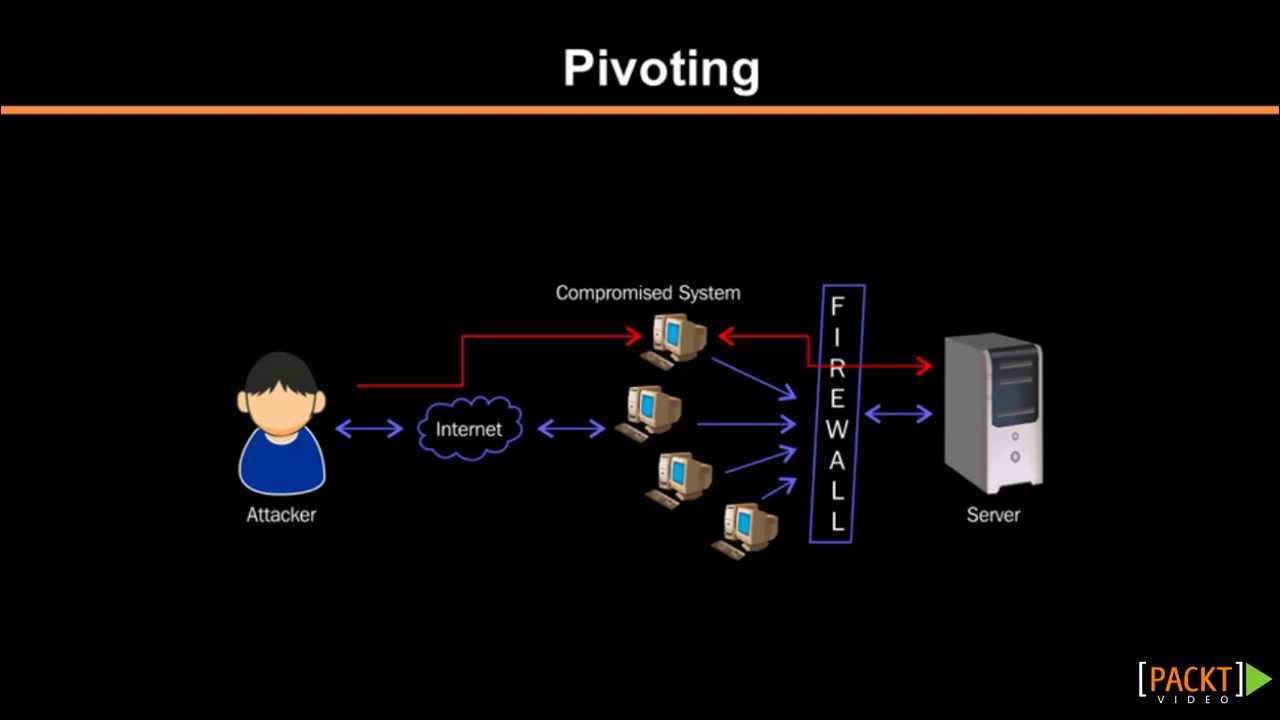
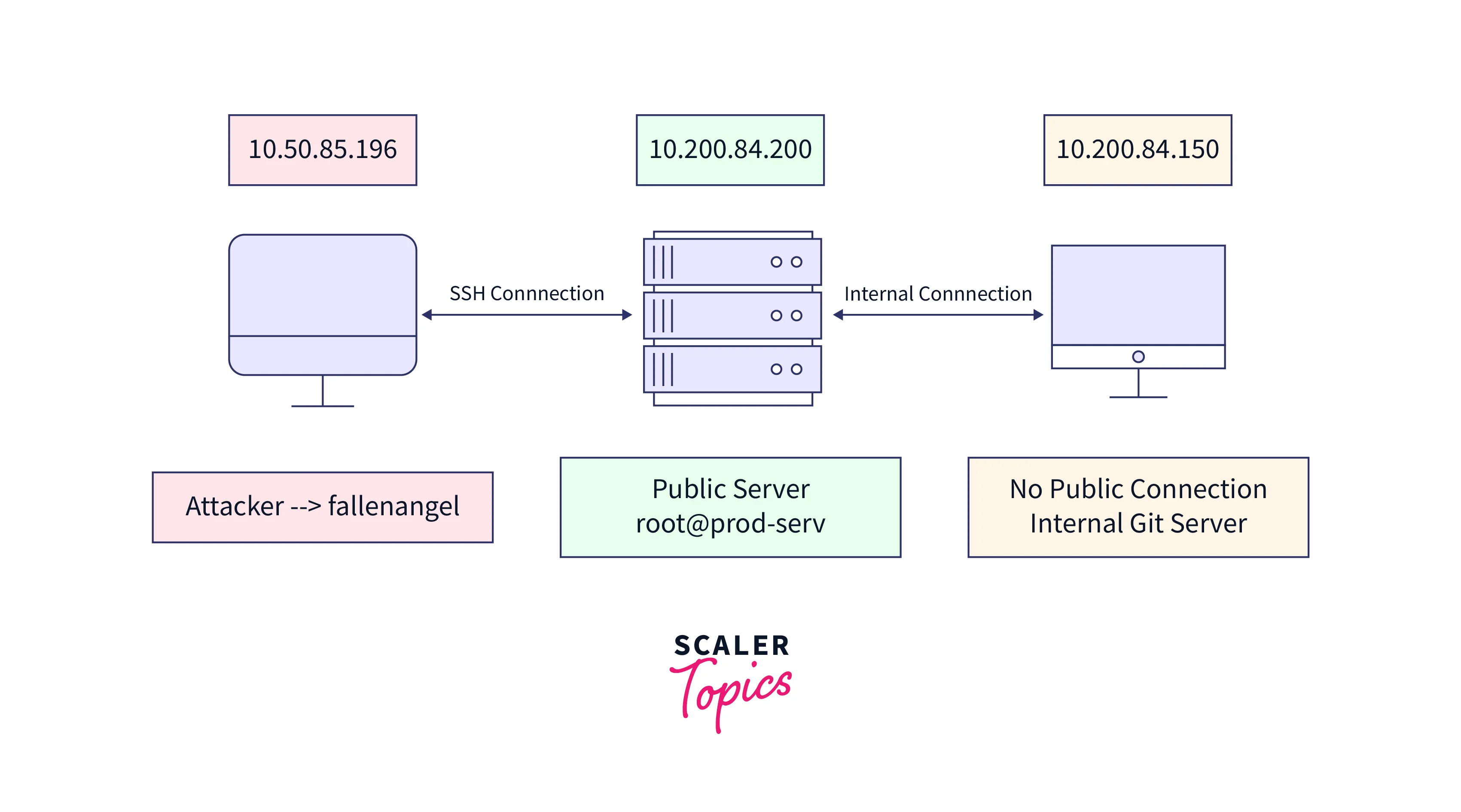
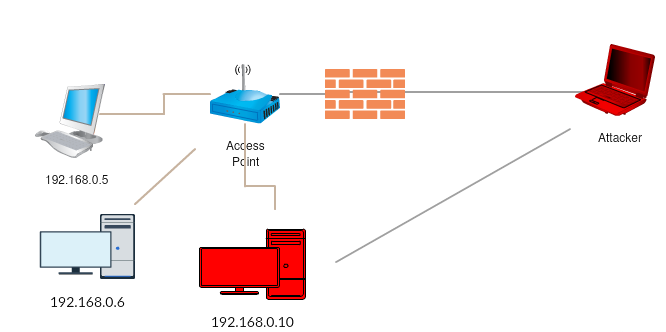
Web Security Geeks - The Security Blog: Metasploit Pivoting And Port Forwarding : Attacking Network - Pentesting Network
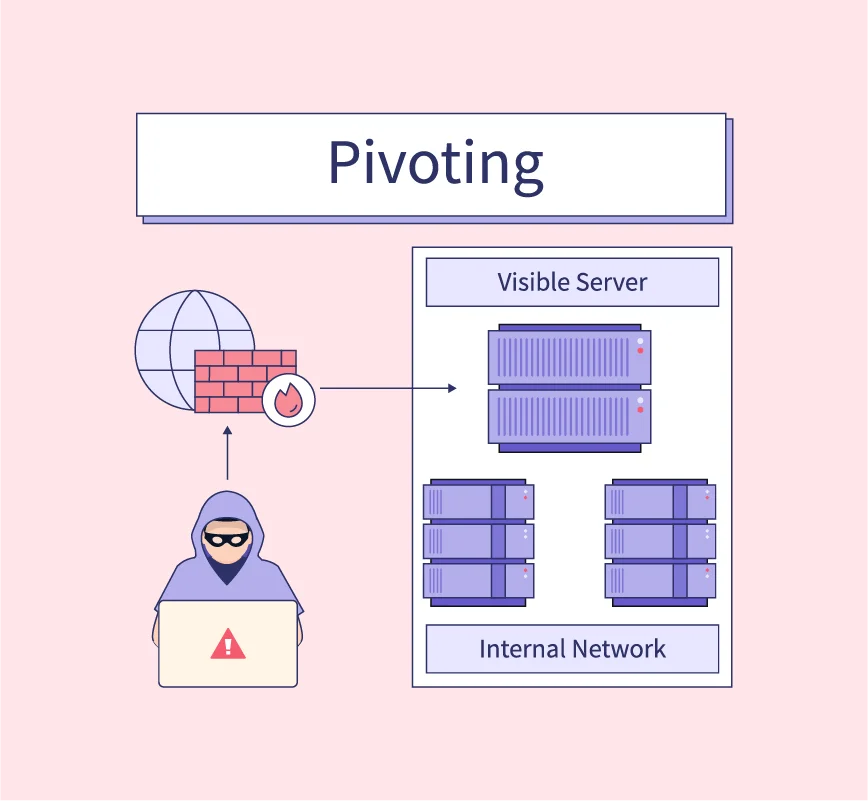
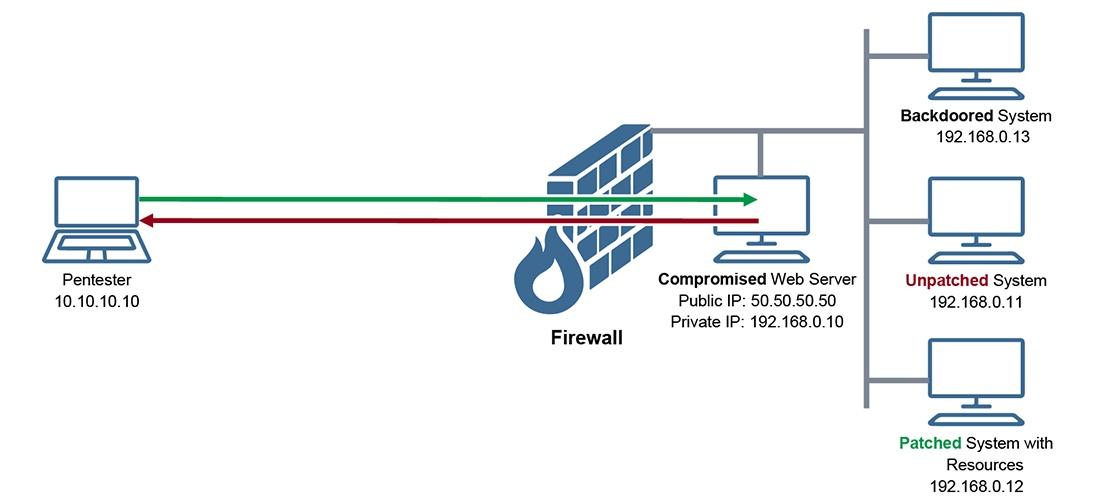
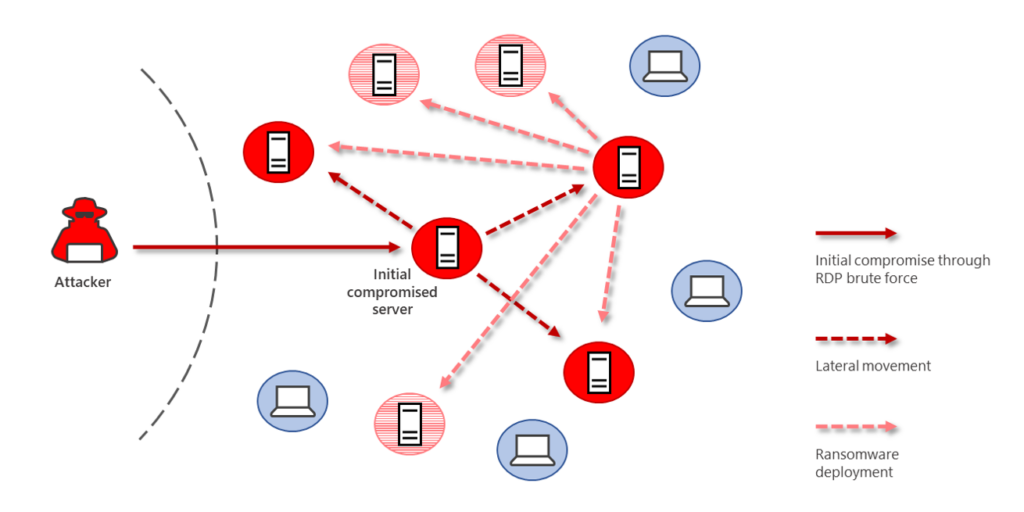
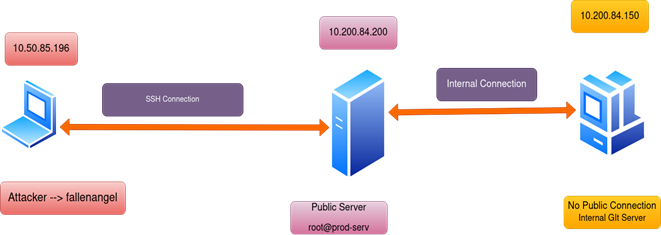
Cybersecurity Pivoting in Penetration Testing: A Practical Guide to Accessing Networks Securely | EC-Council

Cybersecurity PRISM on LinkedIn: Cybersecurity Prism - What Is Pivoting? Pivoting refers to the distinctive…

Hack3rScr0lls on X: "Looking for a stable reverse proxy for pivoting? Check frp! Useful when you've hacked a server and want to establish a channel to the internal network. A lot of

The Pivot Podcast: Cybersecurity & Ethical Hacking Journalist with Hakan Tanriverdi from Bayerischer Rundfunk - Maltego
Cybersecurity Pivoting in Penetration Testing: A Practical Guide to Accessing Networks Securely | EC-Council